Retrieved 18 April — via PRWeb. The LOIC application interface. Attack description Widespread HOIC availability means that users having limited knowledge and experience can execute potentially significant DDoS attacks. However, a single LOIC user is unable to generate enough requests to significantly impact a target. This weeds out illegitimate packets on edge, making certain that only clean traffic reaches the server. 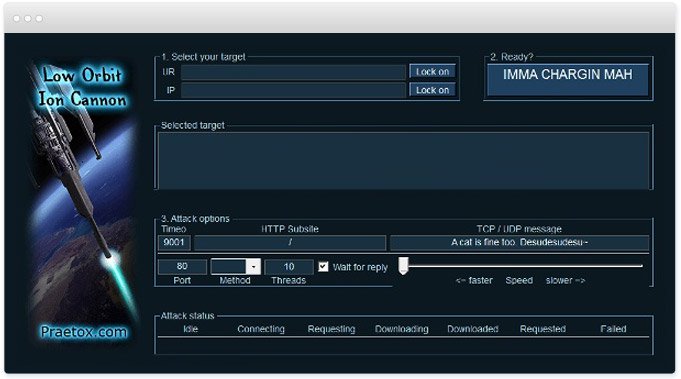
| Uploader: | Kagalar |
| Date Added: | 28 March 2016 |
| File Size: | 27.21 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 52143 |
| Price: | Free* [*Free Regsitration Required] |
Despite booster use, the attack traffic amount generated by HOIC is still not enough for a single user to take down a target system.
High Orbit Ion Cannon - Wikipedia
This basic version of the attack can be customized by using the booster files which follow the VB 6 mixed with VB. HOIC and its predecessor, the LOICare named after an ion cannona fictional directed-energy weapon described as firing beams of ions from a space-based platform onto Earth-based targets. For an attack to in, thousands of users must coordinate and simultaneously direct traffic to the same network.

From Wikipedia, the free encyclopedia. Even though HOIC should, in theory, offer anonymizing through the use of booster files, the actual protection provided is not enough.
Add-on scripts called boosters—not available in the LOIC application—can greatly increase attack magnitude. Detection — HOIC uses booster scripts that let perpetrators scatter attack traffic and hide their geolocation. However, a single LOIC user is unable to generate enough requests to significantly impact a target.
Low Orbit Ion Cannon (LOIC)
In addition, HOIC can simultaneously attack up to domains, making it one of the most versatile tools for hackers who are attempting to co-ordinate DDoS attacks irbit a group. Anonymous were the first group to utilize High Orbit Ion Cannon publicly. It has been speculated that this is due to the notion that Sweden may have stricter internet privacy laws than the rest of the world.
It was launched in retaliation for the shutting down of Megaupload, a filesharing website, and targeted websites belonging to the U. However, such defenses can be overpowered by a coordinated attack that can only be mitigated by a dedicated security solution. They were charged with one count of "conspiracy to intentionally cause damage to a protected computer" for the events that occurred between September 16, and January 2, Attack description Widespread HOIC availability hith that users having limited knowledge and experience can execute potentially significant DDoS attacks.
Primarily, HOIC has been designed as a stress testing tool and can be lawfully used as such to stress test local networks and servers provided the gigh initiating the test has authorization to test and as long as no other networks, servers, clients, networking equipment or URLs are disrupted.
Denial-of-service attacks Free software Public-domain software Public-domain software with source code. This page was last edited on 30 Septemberat InAnonymous petitioned the United States government via We the Peopledemanding that DDoS attacks be recognized as a form of virtual protest similar to Occupy protests.
The Police and Justice Act of the United Kingdom amended the Computer Misuse Actand specifically outlawed denial-of-service attacks and set a maximum penalty of 10 years in prison. The minimalist GUI of the tool makes it user friendly and easy to control. The HOIC application interface. The hivemind version gives average non-technical users a way to give their bandwidth as a way of supporting a cause they agree with.
The popularity came about as it has a version by Anonymous with an IRC based control channel that allows people to join voluntary botnets and attack single targets often led by 4chan or Anonymous themselves. Additionally, its ease of use lets anyone, regardless of knowledge or experience, to execute potentially severe DDoS attacks. As a result their IP addresses are completely visible cannob a target, making them easy to trace. Then a booster file is added which uses.
The basic routine of an attack is to input the URL of the website which is to be attacked, set the power option on low, oebit or high. A high degree of coordination is required among several users. The below version actually contains the Hivemind code too, you just need to launch it with the following option:.
Even though it has allowed attacks to be launched by far fewer users cnanon the older Low Orbit Ion Cannon, HOIC still requires a minimum of 50 users to launch an effective attack and more are required to sustain it if the target website has protection.
How much do you know about DDoS protection? Once launched, LOIC opens multiple connection requests iin a target server. You have just mounted an attack on the target, well done — I guess. Retrieved 6 April Fraud and related activity in connection with computers Government Printing Office".

No comments:
Post a Comment